What Does Ransomware Do to an Endpoint Device
EDR can act swiftly to place such data safely out of harms way thereby containing the threat before figuring out how to neutralize it for good. Endpoint security has evolved from.

New For 2020 Ransomware Defense For Dummies Checklist 2nd Edition Checklist Safety Checklist Infographic
The victims data is held hostage until a ransom is paid.
. You can liken it to societal kidnap activitiesthe criminals capture a victim and ask for a ransom. Ad Ransomware is a problem for organizations of all sizes. A ransom is then demanded to provide access.
EDR containment is all about. Ransomware is a type of extortion attack that destroys or encrypts files and folders preventing access to critical data. Discover the 3 keys things every organization can do now to defend against ransomware.
Hackers might even threaten to erase the data if their demands arent met. Any amount of downtime costs money It can prevent the fulfillment of orders or purchases workflows and communications. It is necessary to secure all the remote devices such as laptops mobile devices and other wireless devices using endpoint security software in order to.
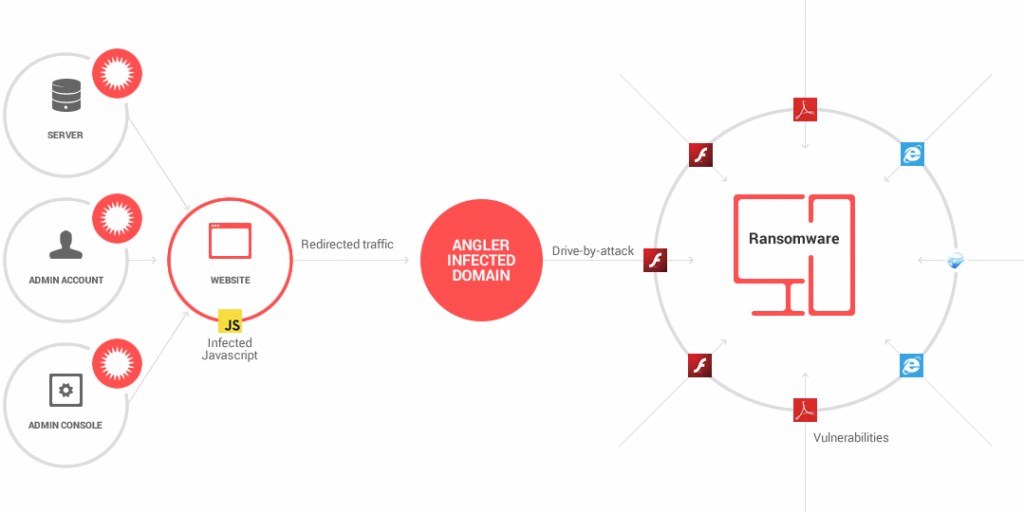
Ransomware is a type of malware Malicious Software that aims to bypass network security protections gain a foothold on endpoint devices or servers discover and spread to other nodes on the network then at some point encrypt the data on devices and servers so that the cybercriminals behind the attack can demand a ransom from the affected organization in. Ransomware is typically spread through spam phishing emails or through social engineering efforts. Businesses utilize them in network security and end-user mobility circles.
Broadly speaking these devices include mobile phones laptops desktops servers tablets workstations and virtual environments. Ransomware infects the endpoint devices and launches attacks on the infected endpoint and other devices connected to the network. Ransomware does affect the entire computers in a network of computers crippling activities until a ransom is paid.
Once in place the ransomware then locks all the files it can access using powerful encryption. Infamous ransomware variants that have caused havoc in the recent past include WannaCry and Cryptolocker. Ransomware is a type of malware attack in which the attacker locks and encrypts the victims data important files and then demands a payment to unlock and decrypt the data.
February 27 2017 - More healthcare organizations are. Ransomware is what it is. Endpoint Detection and Response security platforms use a process that works to detect contain investigate and eliminate malicious cyber threats like ransomware and malware.
Endpoint security systems protect these endpoints on a network or in the cloud from cybersecurity threats. Endpoints are remote computing devices connected to an organizations network. Loss of data downtime of operations damage to brand and reputationeven if a ransom is paidare typical results.
A user or organizations critical data is encrypted so that they cannot access files databases or applications. This type of attack takes advantage of human system network and software vulnerabilities to infect the victims devicewhich can be a computer printer smartphone wearable point-of. Ransomware attacks the endpoint device without the consent of the user or the device discreetly collecting and transmitting information causing harm to the end user.
Ransomware gets accidentally installed in the endpoint device as software. Get our Endpoint Security Software Requirements Template. Endpoint security is the practice of securing endpoints or entry points of end-user devices such as desktops laptops and mobile devices from being exploited by malicious actors and campaigns.
Up to 30 cash back Ransomware and spyware can compromise an organizations most sensitive data so its essential to guard against these threats with the best security. As healthcare ransomware threats continue to evolve organizations must ensure they are securing endpoint devices along with their networks. The goal of a ransomware attack is to bypass network cybersecurity defenses and infect an endpoint device or server.
It goes beyond affecting a single computer data. Learn 3 key things you can do now. Once a foothold exists on a network ransomware will look for other hosts it can jump to and infect.
EDR solutions provide a centralized method in which an organization can monitor endpoints and respond accordingly to keep them secure. First ransomware by its nature inflicts downtime. Ransomware is often designed to spread across a network and target database and file servers and can thus quickly paralyze an.
In the recent years Ransomware attacks have been targeted at corporate levels. Ransomware may enter many different ways but ultimately must compromise the endpoint devices on which data lives. Ransomware is malware that employs encryption to hold a victims information at ransom.
After all it holds data file or entire networks hostage for money. It can also be spread through websites or drive-by downloads to infect an endpoint and penetrate the network. Ransomware is a type of malware that uses malicious software to encrypt data on a victims computer.
And the consequences go well beyond the financial loss of paying a ransom. Commodity ransomware typically spreads like a virus that infects devices and only requires malware remediation. Ransomware can often spread across a network so that it stops productivity across an entire organization.
What does ransomware do.

Firewall Malwaredesign Data Loss Prevention Security Networking

Experience Zero Downtime And Peace Of Mind Peace Of Mind Peace Mindfulness

Soar Use Case Ransomware Attack Sirp

Ransomware Cyber Guarantee Business Stories Cyber Cyber Security

Pin On Internet Technology Security Offers

Best Endpoint Protection Service From Comodo Security Solutions Intrusion Prevention System Device Management

12 Ways To Protect Your Business From A Ransomware Attack Infographic Cybersecurity Infographic Infographic Cyber Security

The Goal Of Endpoint Security Uniserve It Solutions

How Fast Does Ransomware Work What Is The Impact Of Ransomware

Fortinet Ransomware And Phishing Prevention Solutions

Ransomware Detection How To Check Best Ransomware Software

The Basics Of Cyber Security 1 Known About The Latest Cyber Threats 2 Back Up And Syn Cyber Security Technology Cyber Security Awareness Computer Security

Endpoint Security Solution In Dubai In 2021 Security Solutions Solutions Security

Cloud Endpoint Security Cloud Services Cloud Data Protection

We Offer Endpoint Security Unified Threat Management Mobile Device Management Encryption Manager Cyber Security Device Management Mobile Device Management

Ransomware Threats And Endpoint Security An Overview

How To Choose The Best Endpoint Protection Software In 2019 Data Security Diy Security Camera Network Security


Comments
Post a Comment